Continued from Safe Browsing Guide – I
You might get some ‘warnings’ while opening secure pages, like below:
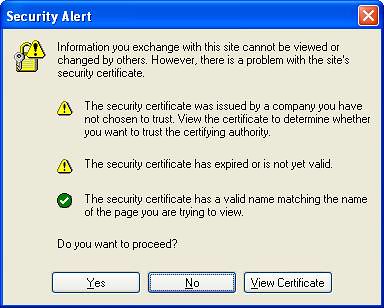
The first one means that the certificate could have been signed by anyone, including by someone you do not trust. If all I need is encryption: for example if I am sending email, and not sending any corporate presentations, or password, or credit card numbers – I should be fine. Many websites use such certificates – but if it’s a bank website using it – I would not login. To give you an idea of the relative security impact of many of the warnings discussed during this guide: this particular warning has a severity of 40 out of 100. It means even on seeing this warning, I am 60% likely to use the website.
The second one means that the certificate has expired. In this case, I would check what is the expiry date (by clicking on the lock) and if it expired a couple of days back I would allow it. In addition, if its sensitive information, I would not use the site until the issue is fixed. This one has a severity of 30.
The last one says that the website names do not match between the certificate and the actual website you are visiting. This could be a case of phishing, and could be serious. What I do in such a case is I find out what name the certificate is issued to (clicking on the lock icon) and check it against the actual website in the URL. If the website visited is server.icicibank.com and the certificate is for icicibank.com – I continue to use the site. If the two are very different, I don’t use the site. Severity is 80.
Mozilla issues one message for each of the issues as noted above while Internet Explorer (shown above) issues just one message with error icons:
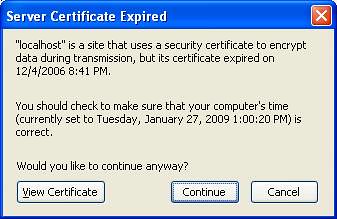
This corresponds to the second warning from Internet Explorer.
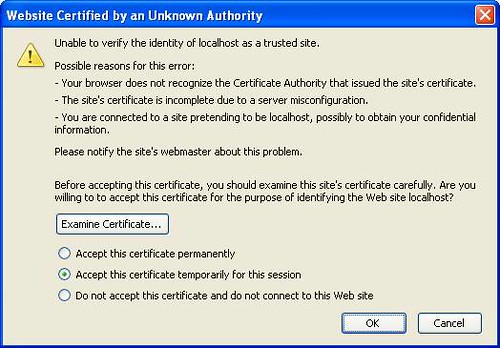
This one corresponds to the first warning from Internet Explorer, same actions apply.
Another warning that you might see is this one:
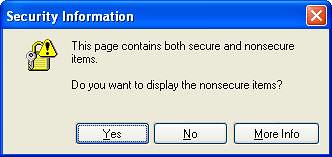
Correspondingly for Mozilla:
This warning means that there is some content on the page which is not encrypted: this could be images or something else. Severity is 50: on GMail it may mean that the emails have such content so it’s ok to continue to do your stuff. However, if on one of the emails you are sending a password – you may want to be careful.
Lastly I would encourage visitors to read this advise on safe browsing from a security expert. This essay from 2004 is still good.
Disclaimer: This is just a guide and is not meant to replace professional advise. No measures can guarantee 100% security. There are a lot of threat vectors outside the scope of this tutorial: such as key loggers on your computer. In addition, the severities explained for warnings are just guides and have no scientific basis.

